mirror of
https://github.com/netbox-community/netbox.git
synced 2026-03-02 04:27:40 +01:00
Increase length of "Custom Fields" #1749
Closed
opened 2025-12-29 16:34:58 +01:00 by adam
·
10 comments
No Branch/Tag Specified
main
21524-invlaid-paths-exception
21518-cf-decimal-zero
21356-etags
feature
20787-spectacular
21477-extend-graphql-api-filters-for-cables
21331-deprecate-querystring-tag
21304-deprecate-housekeeping-command
21429-cable-create-add-another-does-not-carry-over-termination
21364-swagger
20442-callable-audit
feature-ip-prefix-link
20923-dcim-templates
20911-dropdown-3
fix_module_substitution
21203-q-attr-denorm
21160-filterset
21118-site
20911-dropdown-2
21102-fix-graphiql-explorer
20044-elevation-stuck-lightmode
v4.5-beta1-release
20068-import-moduletype-attrs
20766-fix-german-translation-code-literals
20378-del-script
7604-filter-modifiers-v3
circuit-swap
12318-case-insensitive-uniqueness
20637-improve-device-q-filter
20660-script-load
19724-graphql
20614-update-ruff
14884-script
02496-max-page
19720-macaddress-interface-generic-relation
19408-circuit-terminations-export-templates
20203-openapi-check
fix-19669-api-image-download
7604-filter-modifiers
19275-fixes-interface-bulk-edit
fix-17794-get_field_value_return_list
11507-show-aggregate-and-rir-on-api
9583-add_column_specific_search_field_to_tables
v4.5.3
v4.5.2
v4.5.1
v4.5.0
v4.4.10
v4.4.9
v4.5.0-beta1
v4.4.8
v4.4.7
v4.4.6
v4.4.5
v4.4.4
v4.4.3
v4.4.2
v4.4.1
v4.4.0
v4.3.7
v4.4.0-beta1
v4.3.6
v4.3.5
v4.3.4
v4.3.3
v4.3.2
v4.3.1
v4.3.0
v4.2.9
v4.3.0-beta2
v4.2.8
v4.3.0-beta1
v4.2.7
v4.2.6
v4.2.5
v4.2.4
v4.2.3
v4.2.2
v4.2.1
v4.2.0
v4.1.11
v4.1.10
v4.1.9
v4.1.8
v4.2-beta1
v4.1.7
v4.1.6
v4.1.5
v4.1.4
v4.1.3
v4.1.2
v4.1.1
v4.1.0
v4.0.11
v4.0.10
v4.0.9
v4.1-beta1
v4.0.8
v4.0.7
v4.0.6
v4.0.5
v4.0.3
v4.0.2
v4.0.1
v4.0.0
v3.7.8
v3.7.7
v4.0-beta2
v3.7.6
v3.7.5
v4.0-beta1
v3.7.4
v3.7.3
v3.7.2
v3.7.1
v3.7.0
v3.6.9
v3.6.8
v3.6.7
v3.7-beta1
v3.6.6
v3.6.5
v3.6.4
v3.6.3
v3.6.2
v3.6.1
v3.6.0
v3.5.9
v3.6-beta2
v3.5.8
v3.6-beta1
v3.5.7
v3.5.6
v3.5.5
v3.5.4
v3.5.3
v3.5.2
v3.5.1
v3.5.0
v3.4.10
v3.4.9
v3.5-beta2
v3.4.8
v3.5-beta1
v3.4.7
v3.4.6
v3.4.5
v3.4.4
v3.4.3
v3.4.2
v3.4.1
v3.4.0
v3.3.10
v3.3.9
v3.4-beta1
v3.3.8
v3.3.7
v3.3.6
v3.3.5
v3.3.4
v3.3.3
v3.3.2
v3.3.1
v3.3.0
v3.2.9
v3.2.8
v3.3-beta2
v3.2.7
v3.3-beta1
v3.2.6
v3.2.5
v3.2.4
v3.2.3
v3.2.2
v3.2.1
v3.2.0
v3.1.11
v3.1.10
v3.2-beta2
v3.1.9
v3.2-beta1
v3.1.8
v3.1.7
v3.1.6
v3.1.5
v3.1.4
v3.1.3
v3.1.2
v3.1.1
v3.1.0
v3.0.12
v3.0.11
v3.0.10
v3.1-beta1
v3.0.9
v3.0.8
v3.0.7
v3.0.6
v3.0.5
v3.0.4
v3.0.3
v3.0.2
v3.0.1
v3.0.0
v2.11.12
v3.0-beta2
v2.11.11
v2.11.10
v3.0-beta1
v2.11.9
v2.11.8
v2.11.7
v2.11.6
v2.11.5
v2.11.4
v2.11.3
v2.11.2
v2.11.1
v2.11.0
v2.10.10
v2.10.9
v2.11-beta1
v2.10.8
v2.10.7
v2.10.6
v2.10.5
v2.10.4
v2.10.3
v2.10.2
v2.10.1
v2.10.0
v2.9.11
v2.10-beta2
v2.9.10
v2.10-beta1
v2.9.9
v2.9.8
v2.9.7
v2.9.6
v2.9.5
v2.9.4
v2.9.3
v2.9.2
v2.9.1
v2.9.0
v2.9-beta2
v2.8.9
v2.9-beta1
v2.8.8
v2.8.7
v2.8.6
v2.8.5
v2.8.4
v2.8.3
v2.8.2
v2.8.1
v2.8.0
v2.7.12
v2.7.11
v2.7.10
v2.7.9
v2.7.8
v2.7.7
v2.7.6
v2.7.5
v2.7.4
v2.7.3
v2.7.2
v2.7.1
v2.7.0
v2.6.12
v2.6.11
v2.6.10
v2.6.9
v2.7-beta1
Solcon-2020-01-06
v2.6.8
v2.6.7
v2.6.6
v2.6.5
v2.6.4
v2.6.3
v2.6.2
v2.6.1
v2.6.0
v2.5.13
v2.5.12
v2.6-beta1
v2.5.11
v2.5.10
v2.5.9
v2.5.8
v2.5.7
v2.5.6
v2.5.5
v2.5.4
v2.5.3
v2.5.2
v2.5.1
v2.5.0
v2.4.9
v2.5-beta2
v2.4.8
v2.5-beta1
v2.4.7
v2.4.6
v2.4.5
v2.4.4
v2.4.3
v2.4.2
v2.4.1
v2.4.0
v2.3.7
v2.4-beta1
v2.3.6
v2.3.5
v2.3.4
v2.3.3
v2.3.2
v2.3.1
v2.3.0
v2.2.10
v2.3-beta2
v2.2.9
v2.3-beta1
v2.2.8
v2.2.7
v2.2.6
v2.2.5
v2.2.4
v2.2.3
v2.2.2
v2.2.1
v2.2.0
v2.1.6
v2.2-beta2
v2.1.5
v2.2-beta1
v2.1.4
v2.1.3
v2.1.2
v2.1.1
v2.1.0
v2.0.10
v2.1-beta1
v2.0.9
v2.0.8
v2.0.7
v2.0.6
v2.0.5
v2.0.4
v2.0.3
v2.0.2
v2.0.1
v2.0.0
v2.0-beta3
v1.9.6
v1.9.5
v2.0-beta2
v1.9.4-r1
v1.9.3
v2.0-beta1
v1.9.2
v1.9.1
v1.9.0-r1
v1.8.4
v1.8.3
v1.8.2
v1.8.1
v1.8.0
v1.7.3
v1.7.2-r1
v1.7.1
v1.7.0
v1.6.3
v1.6.2-r1
v1.6.1-r1
1.6.1
v1.6.0
v1.5.2
v1.5.1
v1.5.0
v1.4.2
v1.4.1
v1.4.0
v1.3.2
v1.3.1
v1.3.0
v1.2.2
v1.2.1
v1.2.0
v1.1.0
v1.0.7-r1
v1.0.7
v1.0.6
v1.0.5
v1.0.4
v1.0.3-r1
v1.0.3
1.0.0
Labels
Clear labels
beta
breaking change
complexity: high
complexity: low
complexity: medium
needs milestone
netbox
pending closure
plugin candidate
pull-request
severity: high
severity: low
severity: medium
status: accepted
status: backlog
status: blocked
status: duplicate
status: needs owner
status: needs triage
status: revisions needed
status: under review
topic: GraphQL
topic: Internationalization
topic: OpenAPI
topic: UI/UX
topic: cabling
topic: event rules
topic: htmx navigation
topic: industrialization
topic: migrations
topic: plugins
topic: scripts
topic: templating
topic: testing
type: bug
type: deprecation
type: documentation
type: feature
type: housekeeping
type: translation
Mirrored from GitHub Pull Request
No Label
Milestone
No items
No Milestone
Projects
Clear projects
No project
Notifications
Due Date
No due date set.
Dependencies
No dependencies set.
Reference: starred/netbox#1749
Reference in New Issue
Block a user
Blocking a user prevents them from interacting with repositories, such as opening or commenting on pull requests or issues. Learn more about blocking a user.
Delete Branch "%!s()"
Deleting a branch is permanent. Although the deleted branch may continue to exist for a short time before it actually gets removed, it CANNOT be undone in most cases. Continue?
Originally created by @bdlamprecht on GitHub (May 25, 2018).
Issue type
[X] Feature request
Environment
Description
Currently, I have a "one-off" scenario where a certain platform (Juniper EX4550) has the need for a set of interfaces to be "trusted" for QoS purposes. The way my team is accomplishing this is within the
groupssection of thejunosconfiguration (example below).I was able to solve this problem by storing these values in a
custom_fieldnamedspecial_attributes_1and put JSON-formatted data in there. With the length of the field set to be256, it worked just fine when I didn't have more than 16 interfaces to worry about.However, I just came across some devices in our network with MORE than 16 interfaces that I need to account for.
The limit of
256seems to be arbitrary. I understand the concern for not wanting to havecustom_fieldsbe a place to store TONS of information, but I think the current value seems to be quite small.There would be no need to make any changes to the way it is displayed in the WebUI as I'm accessing it via the API. Simply increasing the length from
256to512would be sufficient for my purposes as well as others who may need this for "one-off" scenarios as well.Hopefully, this makes sense and I didn't stretch the limits of what you had in mind for
custom_fields.If you need additional information, please let me know.
The example from the
groupsection of the configuration:(with more than 16 interfaces that need to be "trusted")
Screenshot of how I'm currently solving this in NetBox:
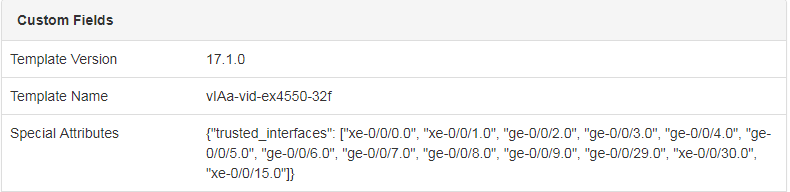
@pm17788 commented on GitHub (May 29, 2018):
@bdlamprecht: As a workaround, how about making these trusted links as inventory items attached to parent device?
It'll have the effect of cleaning up all the main page display view (cosmetic, certainly, but it's a a Something 😁 ), and, the
Inventory Itemsare a multi-valued in that you can have multiple instances of an things with a part idtrusted_link.Another advantage is that you don't have to pack/parse/unpack a text field, but, rather, at API level, you'd query https://netbox/api/dcim/inventory-items/?part_id=trusted_link&device=JuniperEX4550 and get useful data (along with a count, for a cross-check) back? There's also a Description field to be leveraged there, which is useful in that you can feed all kinds of Usefulness into that, too?
@bdlamprecht commented on GitHub (May 29, 2018):
@pm17788 At first I didn't understand what you were referring to, but now I think I have an understanding of what you are trying to communicate. That being said, these "trusted links" are not really (from the NetBox documentation) separate hardware components, but instead, are a logical configuration of the switch chassis.
I like the core idea of NetBox being to document and define how things are supposed to be, and not try and cram things where ever we want them to be just because we can. Using custom fields (I believe) is an appropriate location for this one-off scenario, but I'm limited to the 255-character limit. I'd just like the size of the field to be somewhat larger.
Thanks for the thought though.
@pm17788 commented on GitHub (May 29, 2018):
@bdlamprecht: Fair enough :) Sorry for being unclear. Workarounds are... yeah, well, workarounds :)
@pm17788 commented on GitHub (May 30, 2018):
As a thought, what about having a flag on a custom field which would hide it from the UI view? Still present via API, though.
I find that I have users who just want the WebUI, and for them, an overabundance of custom fields is confusing (especially those which are packed for machine-parseability). The API users I basically don't care about in that if they're using the API, it's on them to filter stuff they don't want to see .
(Edited to explain the rationale)
@bdlamprecht commented on GitHub (May 30, 2018):
Thanks for the suggestion. Perhaps that could be an option as well, but for me personally, I find it confusing when the WebUI and the API don't match (although I could be the minority in that regard).
That being said, I'd like to not mix up requests so if you're wanting that feature, I'd suggest opening a separate issue using the wording you just described.
Cheers.
@1tsi commented on GitHub (Jun 26, 2018):
I just stumbled upon the same kind of problem today with virtual machines, unfortunately there is no such option.
It would be great to have custom text fields with an increased text length.
Best Regards
@jeremystretch commented on GitHub (Jul 2, 2018):
Yes, that's been the goal from the beginning. Custom fields are a convenience allowing you to store a single, small, unique value per field per object. They are not intended to replace a proper templating system or database. Some surefire signs that you're abusing custom fields include trying to set multiple values per field, or setting the same value for all objects in a set.
I encourage you to look into context config data (#1349), which will be available in v2.4. It should fit your particular use case much better.
@bdlamprecht commented on GitHub (Jul 2, 2018):
Yes, I'm aware of #1349 as I'm the one who first opened it and have been waiting axiously for it being implemented (BTW, thanks a ton for getting that working, I haven't had the chance to look into it just yet, but will shortly).
However, I'd like to point out that the use-case scenario for this
jsondata being stored in thiscustom_fieldis in fact a "unqiue value per field per object" and, unfortunately, due to circumstances outside of my control (i.e. customer requirements and vendor stupidity within the same family of switches), I cannot templatize them any more than I already have.Also, concerning this statement:
Just for some background explanation on the use-case for this FR, this is for a switch "template" that has any port within the range of
[ge|xe]-0/0/0to[ge|xe]-0/0/18and[ge|xe]-1/0/0to[ge|xe]-1/0/18(stack of switches) available to connect to equipment that MAY or may NOT support the QoS markings that we require within our realm of management (i.e. trusted or not trusted).My intention is not to be argumentative in any way and I understand that the line has to be drawn somewhere, however, I feel that a limit of
256is still quite low and would like to ask that you take another look at expanding that field slightly.@jeremystretch commented on GitHub (Jul 2, 2018):
Derp. Right, sorry. I've just gotten so used to referring people to it.
The thing is, that's how scope creep works. It's always a slight change, followed by another slight change, and then another and another. NetBox was built to serve as an IPAM/DCIM application, which is already ill-defined territory, and there's constant demand to extend it in myriad directions to fulfill other functions.
@bdlamprecht commented on GitHub (Jul 2, 2018):
Yeah, scope creep is nasty to deal with and is why I said:
I'll see what kind of hacks using duct-tape and bailing-wire I can create to solve the problem.
I appreciate all of what you've done in creating NetBox and getting it to where it is now.
Cheers!